Cloud Security Assessment
A Cloud Security Assessment is an essential process for evaluating the security posture of cloud-based infrastructure, services, and applications. As organizations increasingly depend on cloud service providers (CSPs) for data storage, processing, and application management, understanding and managing the associated security risks is crucial to maintaining robust data protection and operational integrity.
Key Components of Cloud Security Assessment
Risk Identification

The initial phase involves identifying potential risks and vulnerabilities within the cloud environment. This includes assessing the security controls implemented by the CSP and detecting any gaps or weaknesses that could be exploited by attackers.
Compliance Verification
Ensuring adherence to regulatory requirements and industry standards is vital for protecting sensitive data. A cloud security assessment checks compliance with regulations such as GDPR, HIPAA, PCI DSS, and others, helping organizations avoid legal and financial penalties.

Data Security

Data is a core asset, and its confidentiality, integrity, and availability must be preserved. The assessment examines data storage, transmission, and processing practices within the cloud, evaluating encryption, access controls, and data loss prevention mechanisms to ensure robust protection.
Identity and Access Management (IAM)
Effective management of user identities and access controls is crucial for preventing unauthorized access and potential breaches. The assessment reviews IAM policies, authentication mechanisms, and access controls to ensure they are properly configured and enforced.
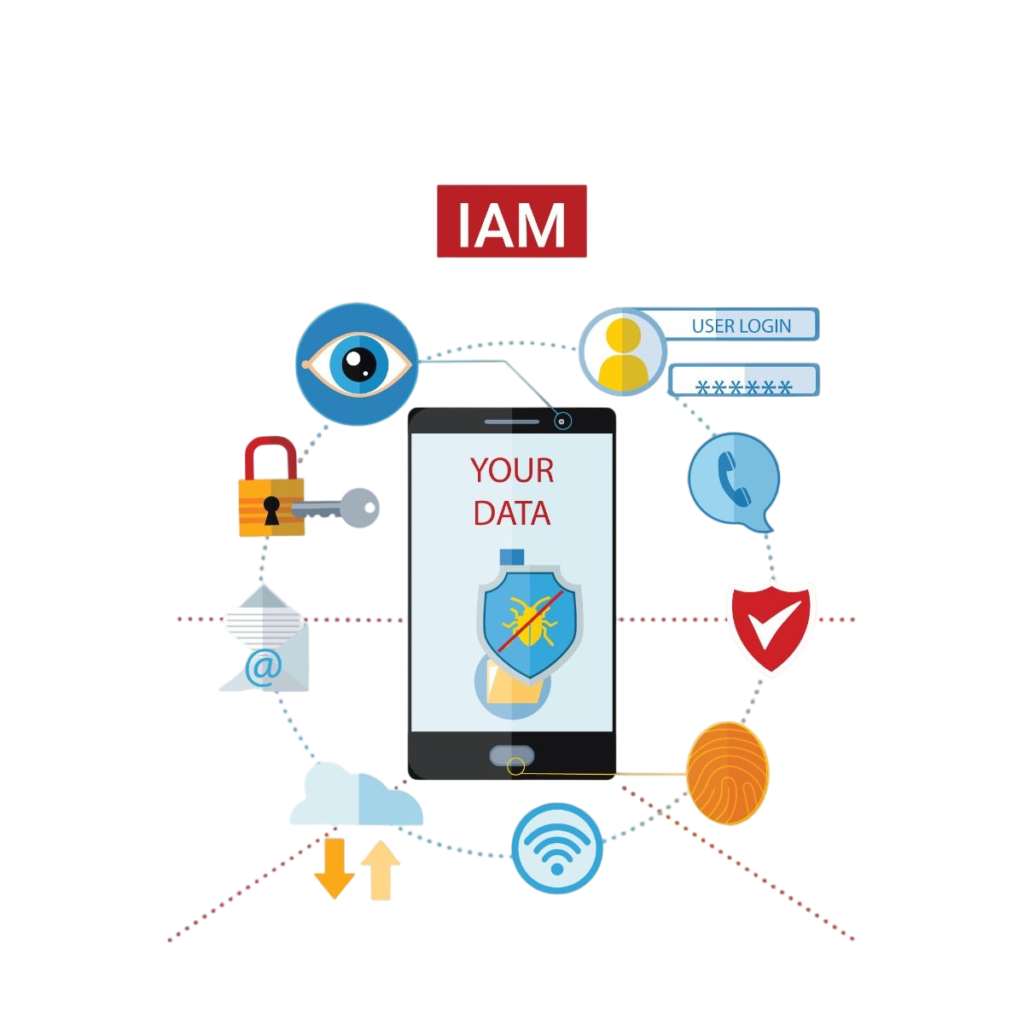
Network Security

Protecting the network infrastructure in the cloud is essential to defend against threats like DDoS attacks, malware, and unauthorized access. The assessment evaluates firewall configurations, intrusion detection/prevention systems, and network segmentation to identify and address potential vulnerabilities.
Incident Response Planning
Despite preventive measures, security incidents can occur. The assessment reviews the organization’s incident response plan, including detection, response, and mitigation procedures for breaches within the cloud environment, ensuring preparedness and effective management of potential incidents.

Benefits of Cloud Security Assessment

Risk Mitigation
Risk mitigation involves proactively identifying and resolving security vulnerabilities to reduce the chances of data breaches, cyber-attacks, and compliance violations. By addressing these issues early, organizations can prevent potential threats from causing harm. This approach ensures better protection for systems, data, and overall operations.
Regulatory Compliance
Regulatory compliance ensures that an organization meets legal and industry standards, avoiding penalties and protecting its reputation. Regular assessments verify that cloud infrastructure aligns with data protection and security regulations. Compliance builds trust and demonstrates a commitment to safeguarding sensitive information.

Enhanced Security Posture
Enhanced security posture means improving an organization’s overall ability to protect data and systems by implementing recommended security measures. Addressing vulnerabilities reduces exposure to threats and strengthens defenses against potential attacks. This proactive approach ensures better protection of sensitive data and critical assets in the cloud.

Cost Efficiency
Cost efficiency in security involves identifying and fixing vulnerabilities early to prevent expensive breaches and downtime. Proactive measures reduce the need for costly remediation, recovery efforts, and legal expenses. Investing in preventive security saves money while ensuring business continuity.

Increased Trust
Increased trust comes from demonstrating a strong commitment to protecting cloud infrastructure and sensitive data through comprehensive security assessments. This reassures customers, partners, and investors of your organization’s reliability and security practices. Building this confidence enhances your reputation and strengthens stakeholder relationships.
Operational Resilience
Operational resilience refers to the ability of an organization to maintain continuous service delivery despite security threats or disruptions. Strengthening cloud security by addressing vulnerabilities ensures systems are more reliable and less prone to outages. This proactive approach supports uninterrupted operations and minimizes downtime.

Continuous Improvement
Continuous improvement involves using insights from cloud security assessments to address evolving threats and adapt security practices. Regular evaluations help organizations strengthen defenses and stay ahead of emerging risks. This proactive approach ensures systems remain secure and resilient against new challenges.
Tailored Security Measures
Tailored security measures involve creating customized recommendations based on an organization’s specific cloud environment and operational needs. This ensures that security controls address unique risks and requirements effectively. Such an approach enhances protection by aligning defenses with the organization’s infrastructure and business objectives.
Improved Incident Response
A thorough security assessment enables the development of robust incident response strategies. By identifying potential vulnerabilities and planning for threats, organizations can respond quickly and effectively to minimize damage during a security incident.
By integrating a comprehensive Cloud Security Assessment into your security strategy, you can safeguard your cloud-based resources, ensure compliance with regulations, and enhance overall operational resilience. This proactive approach helps in effectively managing risks and protecting your organization’s valuable assets in an increasingly complex digital landscape.
